Android developers must protect API keys, passwords, and access tokens from unauthorized access and leakage. Android applications require this sensitive data in the development and production stages. One such example of sensitive data is the Google Maps API key. We will show you how to securely manage this API key in your Android CI/CD workflows using Semaphore, a powerful and flexible CI/CD platform. By following the best practices for managing secrets in Android CI/CD workflows, you can ensure that your sensitive information is protected. Semaphore supports integration with popular source control management tools like BitBucket and GitHub. This allows developers to securely configure secrets and environment variables to store sensitive data. Semaphore provides an intuitive web interface for project management, offering various customization options to meet specific project requirements.
Prerequisites
Please make sure you have the following:
- A Semaphore account. Sign up for a free trial.
- An Android project with sensitive information that needs to be protected. If you don’t have one, you can clone the Google Maps Semaphore project for this tutorial. Learn more about setting up the google maps android project.
Setting up Semaphore
Before we dive into managing secrets in Semaphore, we need to set up Semaphore for our Android project.
- Please check out Getting started with Semaphore.
- Create a new Semaphore project for your Android app. This project will manage your build, test, and deployment workflows.
- On the Semaphore projects page, connect to your Android repository.
- Choose the repository of the cloned Android app.
Step 1: creating a Google Maps API key
First, generate a Google Maps API key to integrate Google Maps into our Android app. Follow these steps to accomplish this:
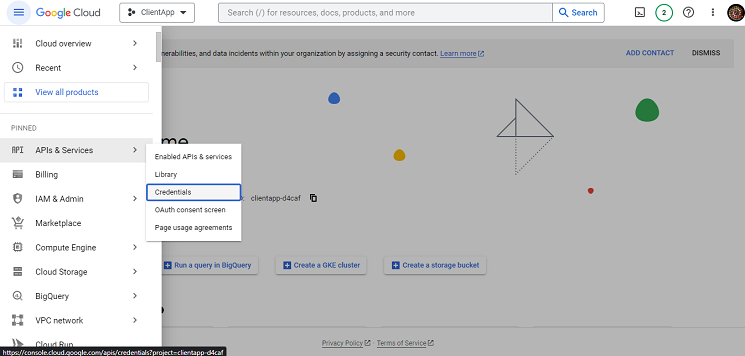
- Start a new project or choose an existing one at Google Cloud Console.
- Select “APIs & Services,” then “Credentials” from the left sidebar.
- Click on “Create credentials” and select “API Key”
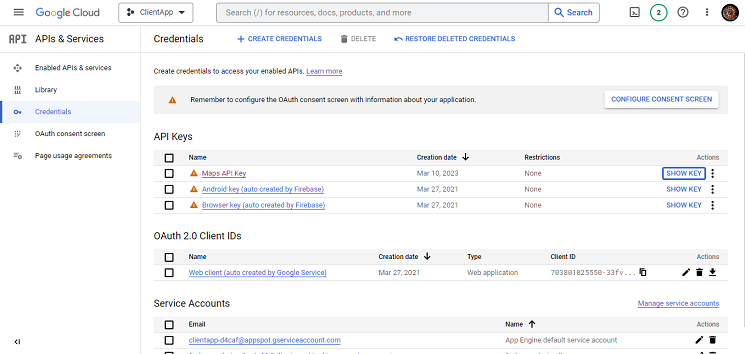
- Copy the generated API key and keep it safe. We’ll use it later.
- To find the Google Maps API key, Select “APIs & Services,” then “Credentials” from the left sidebar.
- Finally, Click “Show Key” to get the Google Maps API Key.
Step 2: creating a secret in Semaphore
Now that we have the API key, we can incorporate it into our Android app. We don’t want to include the API key in our source code for security reasons. Instead, we’ll use Semaphore to manage the API key as a secret.
The first step is to create a secret in Semaphore that will store this sensitive information. A secret is a securely stored encrypted key-value pair that your build and deployment processes can access. Follow these steps to create a Secret in Semaphore:
- In Semaphore, go to the project dashboard.
- In Semaphore project settings, click “Secrets” in the left sidebar.
- Click on the “New secret” button.
- Enter a name for the secret in the “Name of the Secret” field, e.g.
GOOGLE_MAPS_API_KEY - Click on the “Environment Variables” section.
- Enter the name and value of the environment variable in the respective fields.
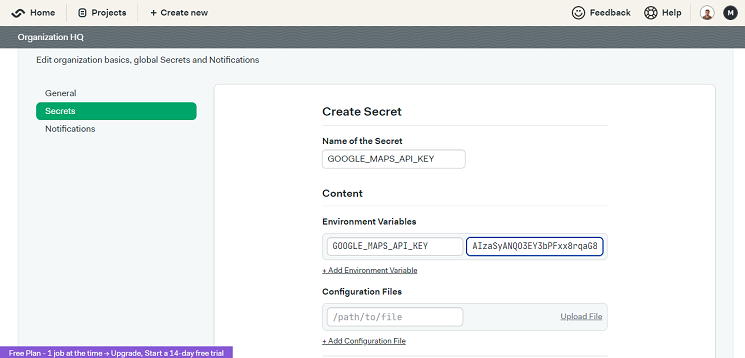
- Click on the “Save secret” button.
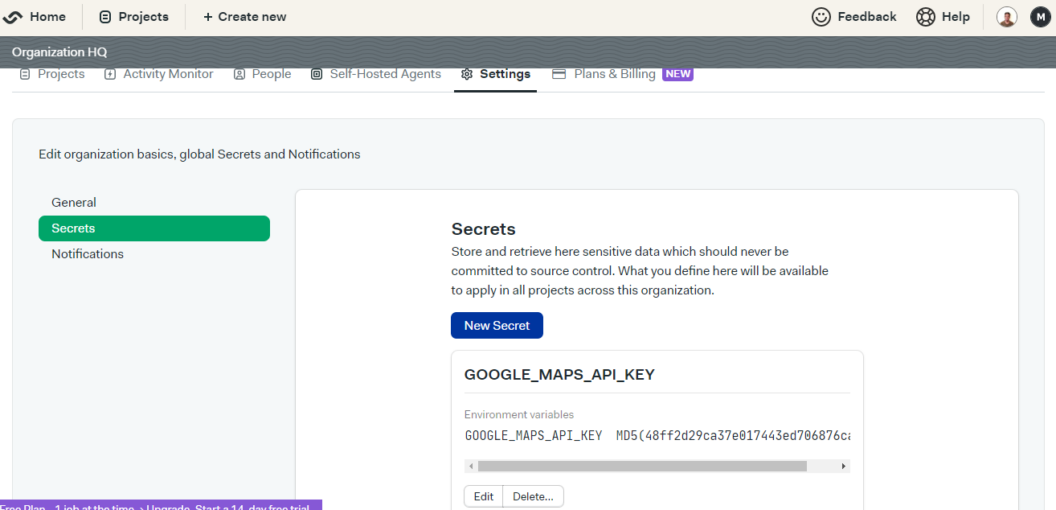
Semaphore will encrypt your secret and store it securely. You can now use this secret in your CI/CD workflows.
Step 3: Activate the secret in a job/block
We need to use the secret in our build process now that we’ve set it up in Semaphore. In your workflow editor for the project, click the Secrets tab and verify that the Google Maps API credentials secret is selected.

Once created, you can activate the secret in the job/block where it is needed, and the environment variables stored in the secret will be automatically imported into the shell without manual creation. To activate a secret in a job/block, follow these steps:
- Open the project page in Semaphore.
- Click the “Edit Workflow” button.
- Select the block in which you want to connect the secret.
- In the right sidebar, find the “Secrets” section.
- Select the secret you want to connect.
- Click “Run the workflow” and then “Start”.
Step 4: Use the secret in your build process
After creating the secret in Semaphore, it’s necessary to integrate it into your build process. To achieve this, you can utilize the envsubst command, which expands the variable’s content in the file before executing the build command.
Here are the steps to use the secret in your build process:
- Open your Android project and find your google_maps_api.xml file. This file belongs in the res/values/ directory.
- Replace the value of google_maps_key.xml with the following:
<string name="google_maps_key" templateMergeStrategy="preserve" translatable="false"> ${GOOGLE_MAPS_API_KEY} </string>3. To substitute the environment variable with the actual value of the secret in your build process, run the following command:
envsubst < app\src\debug\res\values\google_maps_api.xml.template > app\src\debug\res\values\google_maps_api.xml- Finally, build your Android app as usual.
Following these steps, you can use a secret to securely store sensitive information in the source code without exposing it. You don’t have to worry about setting up environment variables independently using Semaphore. The system takes care of it for you automatically.
Implementation of secrets and sensitive data in Android CI/CD
This section will discuss the implementation of secrets and sensitive data in Android CI/CD pipelines. With Semaphore, you can use environment variables in scripts and configuration files, making it easy to convey sensitive data. The deployment process is essential to CI/CD pipelines, and we can automate it using deployment scripts. These scripts are triggered after a successful build and deploy the application to different environments.
Using environment variables in CI/CD
Environment variables store sensitive data such as API keys, access tokens, and other secrets in CI/CD pipelines. Environment variables are a way to pass information to the pipeline without hardcoding the values into the scripts or configuration files. Environment variables are stored in a separate location and not included in the source code or repository, which helps to keep secrets secure.
Incorporation of environment variables in Semaphore
Semaphore is a continuous integration and deployment platform that allows the integration of environment variables in CI/CD pipelines. Semaphore allows the addition of environment variables in the pipeline, used in the scripts or configuration files.
Inline usage of environment variables in Semaphore scripts
Semaphore allows for the inline usage of environment variables in scripts. Inline usage of the environment variables is by prefixing the variable name with a $ symbol. For instance, if the environment variable is API KEY, you can add it to the script by including ${API KEY}.
Use of environment variables in Android build scripts
Android build scripts are scripts used to build and package Android applications. The environment variables store sensitive data and authenticate applications with backend servers. These environment variables can be accessed in build scripts using the aforementioned method.
Automation of deployment process
Automation of the deployment process is an essential part of CI/CD pipelines. The deployment process can be automated using deployment scripts triggered after a successful build. The deployment scripts deploy the application to various environments like staging, production, and testing. Automatic deployment configuration is also a feature that allows for the automatic deployment of the application after a successful build. Automatic deployment configuration is set up in the Semaphore CI/CD pipeline.
Recommendations for managing secrets and sensitive data in Android CI/CD
- Use of an encrypted key: instead of storing secrets and sensitive data in plain text files, or as environment variables in your CI/CD system, it is advisable to use an encrypted key. It’s better to use an encrypted key that only authorized personnel can access. In this way, we can ensure that even if a bad actor manages to get in, they won’t be able to read any important stuff without the right password.
- Restrict access to secrets: in the future, Semaphore plans to introduce a feature allowing authorized personnel to restrict access to secrets and sensitive data using access controls and permissions.
- Avoid hard-coding secrets: avoid hard-coding secrets and sensitive data in your source code, as this makes it vulnerable to unauthorized access.
- Use of temporary tokens: use temporary tokens for authentication and authorization, instead of long-lived credentials (i.e. passwords). This reduces the possibility of unauthorized system access.
Maintaining the security of secrets and sensitive data
- Regular security monitoring and reviewing: It is essential to regularly monitor and review the security of your secrets and sensitive data. This can include checking access logs and reviewing access controls and permissions.
- Store encryption keys securely: encrypt and decrypt encryption keys, secrets, and sensitive data should be kept in a secure location separate from the encrypted data.
Updating secrets and sensitive data
- Regular environment variable updates: update your environment variables and other secrets regularly to ensure they are current and accurate.
- Semaphore automated updating: use automated tools and scripts to update your secrets and sensitive data in Semaphore, ensuring they are always up-to-date and accurate. You can use Semaphore’s CLI tool and a simple Bash script to automatically update your secrets and sensitive data. Keep your secrets and sensitive data safe by following these best practices.
Conclusion
In conclusion, managing sensitive data such as API keys, passwords, and access tokens is essential for Android developers. It protects such information from unauthorized access and leakage during the development and production stages. Semaphore, a flexible CI/CD platform, provides an intuitive web interface and various customization options for securely managing secrets and environment variables. By following the best practices for managing secrets in Android CI/CD workflows, developers can use Semaphore to automate their build, test, and deployment processes. Thus, sensitive information is kept safe at all times. This tutorial has shown you how to securely manage the Google Maps API key in an Android CI/CD workflow using Semaphore, applied to various secrets and sensitive configuration files.
Very informative and well explained..